It can be easy to sell some products to several customers. But it is much more challenging to sell a large amount to a business.
It can be even more demanding with Magento stores as although online business is no strange term, it is still relatively new.
We all know the importance of user experience in the B2B world. To improve such experience, we need the right tools for more quality features.
That is why we have shortlisted the 7 Best Magento 2 Extensions for B2B here, each one dealing with a different aspect of the whole journey.
Let’s check them out!
Top 7 Outstanding B2B Magento 2 Extensions for 2019
Price: $159 → $119 with 1-Year Free Support and Free Lifetime Update
Review: 4.7/5 – 39 Reviews
With new updates and features, Magento 2 Extension 2019 Wholesale Fast Order by BSS Commerce offers a faster and more seamless purchase experience for customers.
Ranking at the top of Quick Order Extensions by SKUs/ product names, this module comes in handy for reducing time for product selection.
These days, wholesale customers want self-service and expect to make bulk orders by themselves rather than wait to be served on the standby list.
Therefore, you should put everything at their fingertips to fasten the ordering process and increase conversion rates!
What is that special about Self-Service in eCommerce?
- A streamlined process from Searching to Ordering
- Faster purchase decisions, no more waiting for phone or fax
- A visual and clear ordering management
- Less cost for a sales support team
Key features offered:
- Fast order with SKU: This extension is the only bulk order module that offers 2 templates of quick order form, both of which are optimized for the best B2B experience.
- Use CSV for Bulk-Add to Cart: Wholesale customers normally already have a sheet of their preferred products and quantities etc.
- Advanced field for quick order: Alternatively, customers can also enter multiple SKUs and their quantities in this field just by this simple form: ‘SKU:quantity’, one SKU per line.
- Quick order for various product types: This works especially well with products with custom options. Popups are displayed smartly with back & forth buttons.
- Easy Settings of Fast order form: The features are almost plug ’n play so configurations can be set up in a matter of minutes. You can also choose to apply the Quick Order for different customer groups.
# 2. Magento 2 Share Cart by MagePlaza
Price: FREE – no Support
Review: 4.8/5 – 6 Reviews
The Magento 2 Extension 2019 Share Cart by Mageplaza enables customers to share their shopping experience with their friends and family.
In the case of business customers, the shared cart can get to other people in the sales team or other managers within the business.
The module is certainly an easy way of doing Marketing through existing customers and enhancing conversion rates.
Each customer’s cart has a different link, which can be shared anywhere and anybody can see without any restriction.
So what are the benefits of a shared cart in this Magento B2B Extension?
- Sharing favorite products with others: Instead of words or captured images, the whole cart shared is a brighter recommendation.
- Saving order and purchasing data: The information can be saved in the form of a PDF for future review and analysis.
- Promoting the store conveniently: Recommendations from friends and family are easily trusted. Business customers can also make suggestions for their partners.
Key features offered:
- A ‘Share Cart” Button: This button appears on both Mini-cart and Shopping Cart Page. The link copied is the fastest way of sharing cart information. Also cart content is auto-updated so the link will still work when there are changes in the cart.
- ‘Text’ Button for Quick Summary: The text pop-up looks simple but is handy for an overview of the cart content like product name, SKU, quantities, and cart total.
- ‘PDF’ Button for Cart Download: The PDF provides more information than the text pop-up. Included are the store’s information like name, address, phone, etc. And more importantly, purchasing date and summary are also added.
# 3. B2B eCommerce Suite by IWD Agency
Price: Subscription Fee charged Monthly: Gold – $500; Silver – $250; Bronze – $50.
Review: 4.5/5 – 8 Reviews
As one of the best Magento 2 extensions for e-commerce, this Magento B2B Extension has a lot more features to offer to us.
The module covers the whole B2B customer journey, from registration to checkout. It is also compatible with all the best Magento 2 versions available, even fits Magento 1 as well.
Besides, there are a bunch of new features which shall surely catch your interest like:
- Advanced management of custom quote requests
- Active sales-boosting with salesforce team
- Credit limits for wholesalers
- Manage roles of sub-accounts for businesses
- Company account administers orders submitted by sub-accounts
- Display of Marketing materials on B2B Dashboard
Key features offered:
- Powerful B2B tools integrated: The B2B tools and workflows offered are meant to enlarge your Magento store and upgrade it to the next level. The advanced features included are account credit limitations, a robust ordering matrix, quoting functions, etc.
- Gated access for B2B customers: A customized login page for wholesale customers only can be set as a part of the default page or as a separate one. Customizable Dashboard for your wholesalers: The B2B portal offers a wide range of ordering workflows for your customers so that they can manage their shopping cart and order history more easily.
- Faster Bulk Order: The Suite’s customized fast order tables enable customers to find and add products at lightning speed. Quick preview and adjustments are also within easy reach while your wholesalers need not go to any other pages.
- Quick Order with CSV files: Encourage your wholesalers to make bulk orders by uploading their spreadsheet with their choices of products and quantities directly to the B2B Dashboard. This gives them more time and activeness.
# 4. Magento 2 Catalog Permission by BSS Commerce
Price: $99 with 1-Year Free Support and Free Lifetime Update
Review: 4.7/5 – 42 Reviews
The Magento 2 Extension 2019 Catalog Permission enables store admin to assign different access to specific product categories and CMS pages for different customer groups. If customers are not granted suitable rights, they might get stranded.
Besides restricting access, the extension can also get non-authorized customers back to specific URLs that might meet their needs.
The extension might not be richest in features compared to others in the market but it is the most easy-to-config one.
Key features offered:
- Limit access to categories by customer groups: The category configuration page now has a tab called Catalog Permission, in which access is granted accordingly for customer groups.
- Different Catalog Permissions for Parent and Sub-Categories: The extension gives admin freedom to apply settings, meaning it is up to them to grant the same restrictions of parent categories to the child ones or not.
- Limit access to CMS Pages by customer groups: Similar to product categories, admins can also grant different access to customer groups, like restricting the ability to view Refund Policy Page for not-logged-in customers.
- Redirect customers to a specific URL: A tailored message would do well for notifying customers of catalog permissions. Then guest viewers can proceed with registering a B2B account.
- Besides, the extension allows disabling any product belonging to a restricted category. It is also possible to disable a category from the menu and layered navigation.
# 5. Magento 2 Quotation Manager by Cart2Quote
Price: Various payment options: One-off Price or Subscription and different business levels. The lowest one is the Lite version, €8.25/ Month or €199 for a one-time payment.
Review: Customers are mostly clients so no rating information is available.
The Magento 2 Extension 2019 Quotation Manager by Cart2Quote is one of the best Magento 2 Extensions for Quotation. It allows you, wholesale store admins, to receive quotes quickly and negotiate prices with customers.
Key features offered:
- Easy quote creating: Allow your customers to submit a quote request through a handy form. You can also set rules for quotability per product, customer group or store.
- Efficient management of quote requests: Handle quotes and convert them into orders. You manage them all from the backend, from negotiating with customers to confirmation of orders.
- Offering better price deals: The two-way communication between store owners and customers are feasible with the help of Magento built-in CRM tool.
The Magento B2B Extension also provides a flawless front-end experience for wholesalers with all fully customizable fields, user-friendly quick quote form, and built-in templates, including default and RWD themes.
It also assures a seamless administration experience for store owners. The features offered are quick quotes, easy profit analyzing, and instinctive CRM features.
# 6. Magento 2 Ajax Add to Cart and Quick View by Weltpixel
Price: $0 for Free Version with Limited features and $149 for Pro Version with full features.
Review: 4.7/5 – 22 Reviews
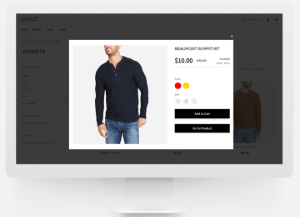
The Quick View Magento 2 Extension 2019 by Weltpixel allows customers to take a quick look at the product details without actually opening their pages. This function can be set on any button, image, product or widget, even products on CMS pages or lookbook hotspots.
Furthermore, the quick look function enables quick adding products to cart without loading new pages. Instead, a popup window will show all the product details.
It is easy to configure from backend as you can set product zoon and visibility of specific elements for quick-view.
Key features offered:
- Choose to hide or display certain product elements on quick view popup: (thumbnail) image, SKU, quantity selector, short description, etc.
- Pick a style for quick view button
- Display ‘Go to product’ button on the quick-view frame
- Set quick view to auto-close X seconds after the product has been added
- Allow auto-scroll to top and auto-open quick cart
- Provide a new popup with buttons like ‘Continue shopping’ or ‘Proceed to Checkout’
- The quick-view function can be added to any button on the website and linked to any specific product.
- For Pro Version only: SEO, quick view position control, and hotspot functionalities
Configuration options in this Magento B2B extension are all easy to set, including changing the quick-look box with Custom CSS, control over specific buttons and other settings.
# 7. Magento 2 Shipping and Payment Method by Customer Group by BSS Commerce
Price: $99 → $79 with 1 Year Free Support and Free Lifetime Updates
Review: 4.7/5 – 43 Reviews
Checkout is the make-or-break step of an order, thus it is supposed to be smooth and convenient, especially with payment and shipping options.
The objective of this extension is to improve checkout for customers and management for store admins.
The default function by the best Magento 2 extensions offers a lot of shipping and payment methods.
However, they do not always work for different countries, order quantity or status, and especially customer groups.
Key features offered:
- Shipping Methods per Customer Groups: Allow store owners to set different shipping options for different customer groups. This helps with your promotions and customer loyalty.
- Payment Methods per Customer Groups: Payment should always be made convenient, yet still ensure security. People now prefer online and quick payment options, so you should put them all at their fingertips.
With these simple but essential settings, you can now manage your checkout process better for your customers, and no more messing with complaints from ‘Sorry, Sir. This shipping or payment option is currently not available.’!
The Last Few Words
The above B2B extensions listed are meant to help you improve your customer journey. Happy B2B trading!