Because of the personal, payment and credit card information that is required to complete a sale, hackers are always aiming to eCommerce sites. When a website is hacked, customers might suffer money loss and private identity theft, and merchants suffer lost of merchandise, their reputations collapse. In this guideline, we will describe a multifaceted approach to enhance the security system of your Magento installation, so you can make your online store secure and avoid being hacked.
Choose the reliable hosting providers and solution integrators. When checking their qualifications, check their approach to security. Make sure that they pentest their code for security issues, and they have a standard secure software development life cycle, for example, The Open Web Application Security Project (OWASP).
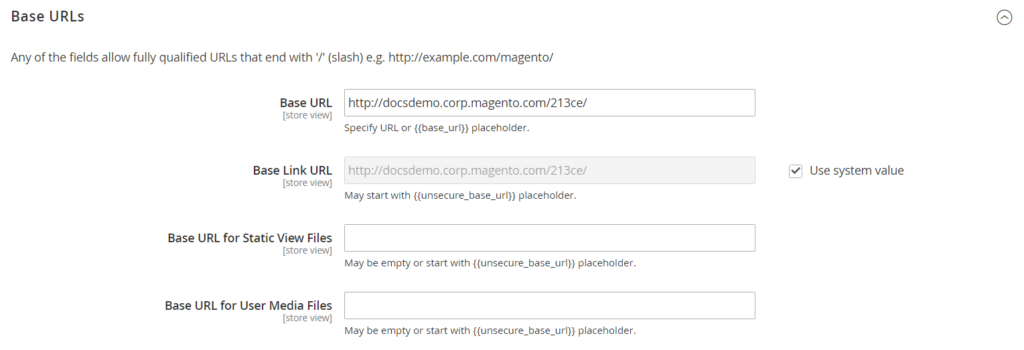
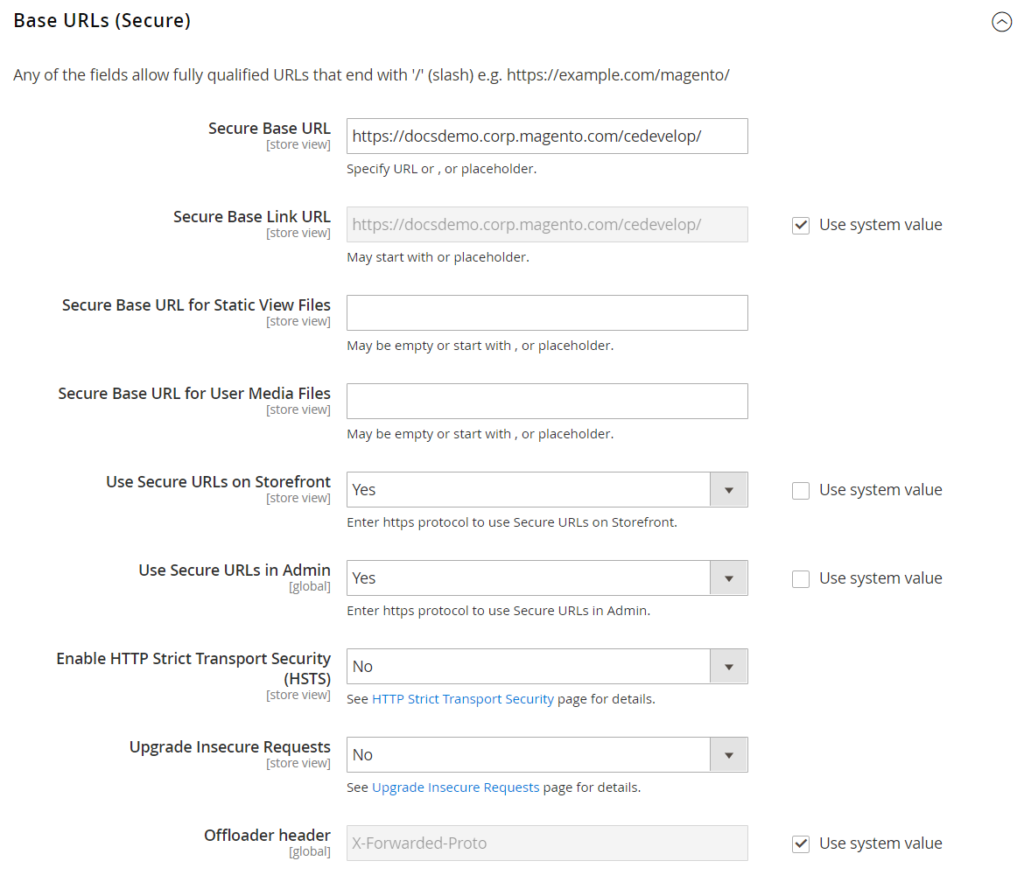
Launching your site or upgrade to run it over securely, encrypted HTTPs
Update all software and security patches on your server, including other websites and database software.
Server Environment
|
Secure the server operating system. Your hosting provider must ensure that they do not install any unnecessary software on the server. |
|
Manage files using SSH/SFTP/HTTPS, and disable FTP. |
|
To protect system files when using the Apache web server, Magento includes .htaccess files. If you use another web server such as Nginx, make sure to protect all system files and directories. For a sample Nginx configuration, see magento-nginx.conf on GitHub. |
|
Use secure and unique passwords (at least 20 characters including uppercase, lowercase, numbers, and symbols) and change them periodically. |
|
Update the software and security patches. |
|
Check any issues that are reported for software components used by your Magento installation, including the operating system, MySQL database, PHP, Redis (if used), Apache or Nginx, Memcached, Solr, and any other components in your specific configuration. |
|
Restrain access to the cron.php file to only required users. For example, restrict access by IP address. If possible, block access entirely and execute the command using the system cron scheduler. |
Advanced Techniques
|
Automate the deployment process, if possible, and use private keys for data transfer. |
|
Restrain access to the Magento Admin by list all IP address of computers that are authorized to use the Admin and Magento Connect downloader. To know how to whitelist IP addresses, please read: Secure Your Magento Admin. |
|
Do not install extensions directly on a production server. Block or remove access to the /downloader directory to disable the Magento Connect downloader on the production site. Use the same whitelisting methods if necessary. |
|
Use two-factor authorization for Admin logins. Some extensions provide additional security by requiring a generated passcode on your phone or a token from a particular device. |
|
Check your server for “development leftovers.” Clear all available log files, publicly visible .git directories, tunnels to execute SQL, database dumps, phpinfo files, or any other unprotected files that are not required, and might be used for hacking. |
|
Restrain outgoing connections to only those that are required, such as for payment integration. |
|
Use a Web Application Firewall to block all suspicious traffic, such as credit card information being sent to a hacker. |
Server Applications
|
Secure all applications running on the server. |
|
Try not to run other software on the same server as Magento, especially if it is accessible from the Internet. Vulnerabilities in blog applications such as WordPress can leak personal information from Magento database. Install such software on a different server or virtual machine. |
|
Update the software and security patches. |
Admin Desktop Environment
|
Secure the computer that is used to access the Magento Admin. |
|
Update your antivirus software, and use a malware scanner. Do not install any unknown programs, or click suspicious links. |
|
Use a password manager tool, for example, LastPass, 1Password, or Dashlane to create and manage secure, unique passwords. Use a secure password to log in to the computer (20 characters including uppercase, lowercase, numbers and special characters), and change it periodically. |
|
Do not save FTP passwords in FTP programs, because they are often penetrated by malware and used to infect servers. |
|
Update the Magento installation and security patches to enhance security. |
|
Use a unique, custom Admin URL to avoid to scripts that try to hack into every Magento site.
Check with your hosting provider before using a custom Admin URL. Some hosting providers require a standard URL to meet firewall protection rules. |
|
Block access to any development, staging, or testing systems. Use IP whitelisting and .htaccess password protection. When compromised, such systems can produce a data leak or be used to attack the production system. |
|
Use the correct file permissions. Set core Magento and directory, including app/etc/local.xml files to read-only. |
|
Use a secure password for the Magento Admin (20 characters including uppercase, lowercase, numbers and special characters). |
|
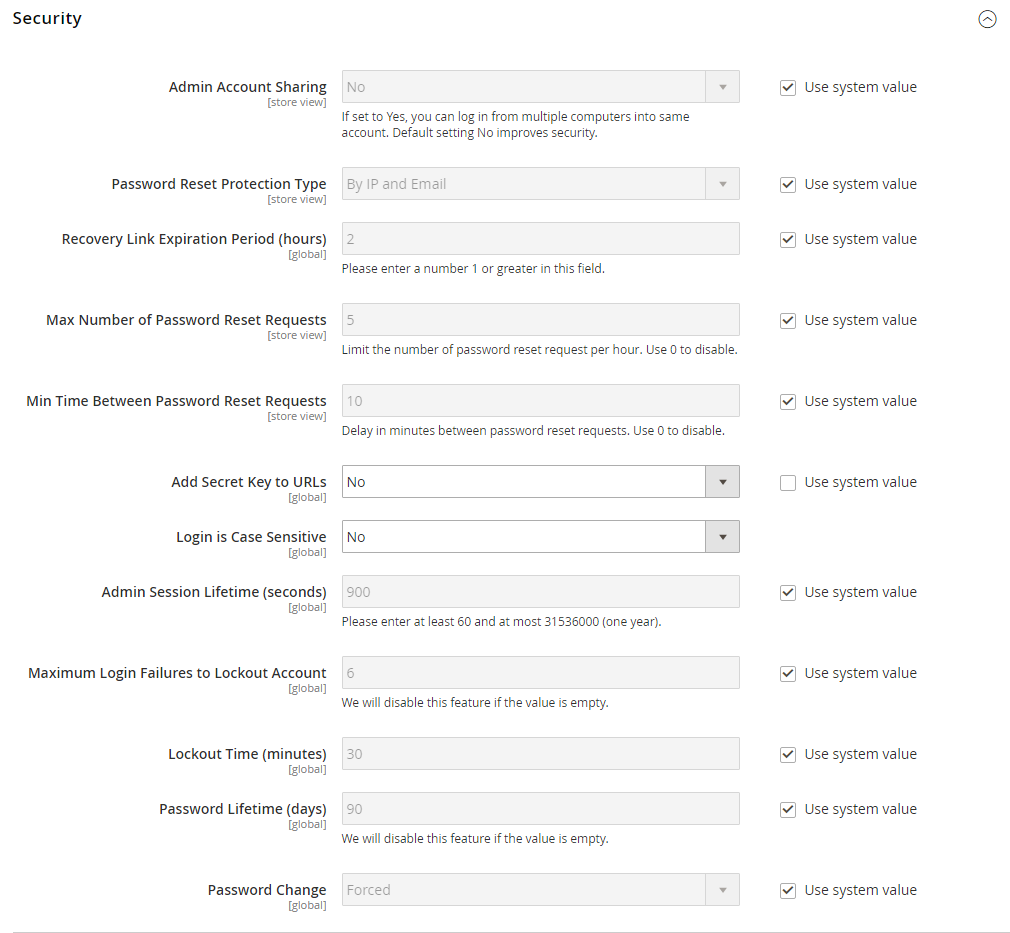
Use all security-related configuration settings of Magento for Admin Security, Password Options, and CAPTCHA. |
- Don’t be Taken for a Ride
|
Only download and install extensions from trusted sources. Review extensions for security issues before installing them. |
|
Do not click suspicious links or email. |
|
Do not unveil the password to your server or the Magento Admin, unless you are required to do so. |
|
Build a disaster recovery/business continuity backup plan. |
|
Backup your server and database automatically to an external location. A typical setup requires daily incremental backups, with a full backup on a weekly basis. To verify that data can be restored, test the backup regularly. |
|
For a large site, simple text file dumps of the database take a long time to restore. To deploy a professional database backup solution, work with your hosting provider. |
- Monitor for Signs of Attack
To check for signs of attack, complete a security review periodically, and also when contacted by customers with security-related concerns.
Security Review
|
Check for unauthorized Admin users periodically. |
|
Use automated log review tools such as Apache Scalp. |
|
To install and set up an Intrusion Detection System on your network and review server logs for suspicious activity, work with your hosting provider. |
|
Use a file and data integrity checking tool such as TripWire to receive notification of any potential malware installation. |
|
Monitor all system logins (FTP, SSH) for unexpected activity, uploads, or commands. |
- Follow Your Disaster Recovery Plan
In case your website is compromised, work with your IT security team, hosting provider and system integrator to decide the scope of the attack. Focus on consideration the type of compromise and the size of the store. Then, adjust the following recommendations to your business needs.
- Block access to the site, so the hacker cannot erase evidence or steal more data.
- Backup the current site, which will include evidence of the installed malware or compromised files.
- Determine the scope of the attack. Was credit card data accessed? What type of data was stolen? Was the data encrypted? How much time has passed since the compromise? Typically you can expect the following types of attack:
| Deface |
Site access is compromised, but often the payments information is not. User accounts might be compromised. |
| Botnet |
Hackers use your site as a botnet that spams email. Although data is not compromised, your server is blacklisted by spam filters. |
| Direct Attack on Server |
Data is compromised, malware and backdoors are installed, and the site is down. Payment information – provided that it is not stored on the server – is probably safe. |
| Silent Card Capture (Phishing) |
Hackers install hidden malware or card capture software or possibly modify the checkout page to phishing credit card data. Such attacks can go secretly for a long time, and result in a significant compromise of customer accounts and financial information. |
- Try to find the attack vector to decide how and when the site was compromised. Read server log files and file changes. Sometimes there are multiple different attacks on the same system.
- If possible, format and reinstall everything. In the case of virtual hosting, create a new instance. Malware might be hidden in an unsuspected location, just waiting to restore itself. Remove all unnecessary files. Then, reinstall all required files from a known, clean source.
- Update security patches.
- Reset all credentials, including the database, file access, payment and shipping integrations, web services, and Admin login.
- If payment information was compromised, it might be necessary to contact your payment processor.
- Contact your customers about the attack and the type of information affected. If payment information was compromised, they should check for unauthorized transactions. If personal data including email addresses was compromised, they might be targeted with phishing or spam.